What is DSPM? Data Security Posture Management Guide
February 1, 2023

Data Security Posture Management (DSPM) refers to the practice of assessing and managing an organization's overall data security posture. It involves monitoring, evaluating, and continuously improving the effectiveness of data security controls and measures in place to protect sensitive information. DSPM provides a holistic view of an organization's data security status and helps identify vulnerabilities, gaps, and areas for improvement.
By actively managing data security posture, organizations can enhance their ability to protect sensitive data, minimize security risks, detect and respond to threats promptly, and meet regulatory compliance requirements. DSPM plays a crucial role in maintaining data confidentiality, integrity, and availability while ensuring the overall security and resilience of an organization's data infrastructure.
Data security is a prerequisite
Data security is an essential requirement in today's digital landscape. Organizations must prioritize data security to protect sensitive information from unauthorized access, breaches, and misuse.
Privacy laws require organizations to take appropriate measures to protect consumer data. Additionally, breaches and privacy violations result in financial damage and cause irreparable damage to a company's reputation and loss of customer trust.
With the world taking data privacy very seriously with the advent of laws such as GDPR, CCPA, PIPEDA, etc. countries are enforcing compliance with strict penalties. As a result, sensitive data has become risky and expensive to hold. The new privacy laws, breaches, and privacy awareness have forced many companies to rethink how they collect, store and distribute data. As a result, companies need to actively manage their data security posture.
To compound the issue, as data volume and complexity continue to accelerate inside an organization, delivering data privacy and security is becoming a complex problem. Here are the reasons why data protection is a complex problem.
- In most organizations, personal data is scattered across hundreds of databases and systems, and millions of files. In many companies, personal data is stored in unexpected places such as audio and video formats, images, etc.
- Moreover, personal data moves through many data processing activities spread across an organization. Companies use data as an oil to derive better insights about their customers, and to make sound business decisions to grow and expand their offerings and services.
- Personal data is often shared with business partners outside an organization, making data protection even more complex. Organizations don't have a way to track or monitor their activities. DLP-like solutions are prone to false positives and never have yielded the desired visibility.
- Businesses underestimate the magnitude of their enterprise data and the complexity of their data environment. In our experience, we observe organizations have 100 times more data than they think they do.
De-identifying or deleting all personal data is not practical and defeats the purpose of collecting the data in the first place. Data protection issues remain hidden until a major breach or a privacy incident happens.
Understanding Data Security Posture and DSPM
To determine your data security posture, your security team needs reliable answers to the following questions.
- What personal data do we have?
- Who has access to it?
- Who is using the data?
- What data assets/sources pose the highest breach risk?
- What are the factors driving higher breach risks? How can we reduce our risk exposure?
- How do we secure personal and sensitive information to eliminate data privacy and compliance risks?
Once you understand the current state of your data, you can eliminate hidden issues and avoidable risks that can dramatically impact your data security.
Data Security Posture Management involves the following key components:
- Security Assessments: Conducting regular assessments to evaluate the effectiveness of data security controls, including vulnerability scans, penetration testing, and risk assessments.
- Compliance Monitoring: Ensuring compliance with relevant data protection regulations, industry standards, and internal security policies.
- Incident Response Readiness: Establishing incident response plans and procedures to detect, respond to, and recover from data security incidents effectively.
- Security Awareness and Training: Educating employees about data security best practices, raising awareness of potential threats, and promoting a culture of security throughout the organization.
- Continuous Monitoring: Implementing tools and processes to continuously monitor and analyze security events, network traffic, and user behavior to detect and respond to potential threats in real-time.
- Security Controls and Policies: Implementing appropriate security controls, such as encryption, access controls, data classification, and secure configuration management, based on identified risks and industry best practices.
- Risk Management: Conducting risk assessments and developing risk mitigation strategies to address identified vulnerabilities and threats.
CSPM vs DSPM
CSPM and DSPM were introduced to make cyberspace a safer space. But, their functionalities couldn’t be more different if you tried. Here are some major differences explained below.
.png)
From this, you can tell that CSPM mostly focuses on problems governing the cloud servers and not so much as to what is stored in the cloud. On the other hand, DSPM almost always solely focuses on the security of data.
Protecto provides the best DSPM solutions with granular access to their data and also tokenizing the data so that only a few trusted people can get into it. With RAG (Retrieval Augmented Generation), they constantly update their LLM to current events and ensure the best data security practices.
Why do organizations need a Data Security Posture Management solution?
Organizations need a Data Security Posture Management (DSPM) solution to effectively manage and enhance their data security posture. Here are key reasons why organizations require a DSPM solution:
Comprehensive Visibility:
A DSPM solution provides organizations with a holistic view of their data security posture. It enables them to assess the effectiveness of existing security controls, identify vulnerabilities, and detect potential security gaps across their data infrastructure.
Proactive Risk Identification:
DSPM solutions help organizations proactively identify and assess security risks. By continuously monitoring data systems, networks, and applications, organizations can detect vulnerabilities, misconfigurations, and potential threats in real-time, allowing them to take prompt action before any security incidents occur.
Compliance and Regulatory Requirements:
Compliance with data protection regulations and industry standards is critical for organizations. A DSPM solution helps organizations align with regulatory requirements by providing the necessary tools and capabilities to monitor, evaluate, and demonstrate compliance with data security regulations.
Effective Security Controls Management:
DSPM solutions assist organizations in managing and maintaining their security controls effectively. These solutions offer centralized control and automation capabilities to streamline security configuration management, vulnerability scanning, access controls, encryption, and other critical security measures.
Incident Response and Remediation:
In the event of a security incident, a DSPM solution plays a crucial role in facilitating incident response and remediation. It provides organizations with the visibility and tools needed to quickly identify and respond to security breaches, minimize the impact, and recover systems and data effectively.
Continuous Monitoring and Improvement:
DSPM solutions enable continuous monitoring of data security posture, allowing organizations to stay vigilant against emerging threats and evolving security risks. With real-time monitoring and reporting, organizations can track their security status, measure improvements, and implement necessary adjustments to enhance data security.
Suggested Read: Shadow AI: The Emerging, Invisible Problem Putting Your Company's Data at Risk
Enhanced Collaboration and Efficiency:
DSPM solutions facilitate collaboration between security teams, IT teams, Privacy teams. and other stakeholders. They provide a centralized platform for sharing security information, tracking progress, and coordinating efforts, leading to improved efficiency in managing data security posture.
By implementing a DSPM solution, organizations can enhance their overall security posture, protect sensitive data, and mitigate potential threats effectively.
However, there are several common challenges that organizations may face in implementing Data Security Posture Management (DSPM). Here are some of those challenges:
Data mapping is grossly inadequate:
When everything is a priority, nothing is a priority. Data mapping tools create a laundry list of personal data. Not every personal data is risky and toxic. A list of sources with personal data is not actionable. Data mapping and other tools are inadequate because they only analyze the content of data, while most of the penalties are caused by data use activities and a lack of proper controls. Data discovery tools and traditional processes aren't designed for data protection at today's scale.
Lack of Proper Data Classification:
Data classification is crucial for applying appropriate security controls based on data sensitivity. However, organizations may struggle with the proper categorization and classification of their data, making it difficult to implement effective security measures.
Inadequate Access Controls:
Insufficient access controls can lead to unauthorized access and data breaches. Organizations may face challenges in implementing robust access controls, including user authentication, role-based access control, and privilege management.
Data Loss Prevention:
Preventing data loss is a significant challenge for organizations. Ensuring that sensitive data does not leave the organization's boundaries, whether accidentally or intentionally, requires effective data loss prevention (DLP) mechanisms and strategies.
Security Monitoring and Incident Response:
Monitoring data systems and networks for security incidents and promptly responding to any detected threats is critical. However, organizations may face challenges in implementing comprehensive security monitoring and incident response capabilities, such as the lack of skilled personnel, inadequate tools, or insufficient incident response plans.
Data Protection via Techniques such as Tokenization
Data protection techniques like tokenization play a crucial role in safeguarding sensitive data. Tokenization is a process that replaces sensitive data with non-sensitive placeholders called tokens. Here's how tokenization helps in data protection:
- Enhanced Data Security: Tokenization reduces the risk of data breaches by ensuring that sensitive data is never stored in its original form. Instead, the data is securely stored in a separate tokenization system or vault. Tokens are meaningless and have no inherent value, making them useless if intercepted or compromised.
- Preserves Data Utility: Tokenization maintains the usability and functionality of data while removing its sensitive elements. Tokens can be used for various business processes, such as analytics, application development, or testing, without exposing the original sensitive data. This allows organizations to continue using the data effectively while minimizing privacy risks.
- Reduces Compliance Scope: Tokenization aids organizations in complying with data protection regulations, such as the General Data Protection Regulation (GDPR) or Payment Card Industry Data Security Standard (PCI DSS). By replacing sensitive data with tokens, the scope of compliance requirements is reduced as the original sensitive data is no longer within the organization's systems.
- Simplifies Data Handling: Tokenization simplifies data handling processes, such as data transfers or data sharing with third parties. Since tokens do not contain sensitive information, organizations can securely transmit and share data without compromising its confidentiality.
- Minimizes Insider Threats: Tokenization mitigates insider threats by limiting access to sensitive data. Employees or insiders who handle data may only have access to tokens, reducing the risk of unauthorized data exposure or misuse.
- Facilitates Secure Cloud Adoption: Tokenization is well-suited for cloud environments. By tokenizing data before storing it on the cloud, organizations can maintain control over sensitive information while leveraging the benefits of cloud computing, including scalability and cost-efficiency.
How Protecto can help overcome the limitations of traditional DSPMs
Today, most companies spend their resources inventorying data and securing the perimeter without proper investment and tools to look into data security posture. Protecto is the first Data Security Posture Management (DSPM) solution that not only helps to identify and classify personal and sensitive data, but also helps organizations control their data security posture. We look deep into data and its context, such as who has access and uses the data to determine data security risks.
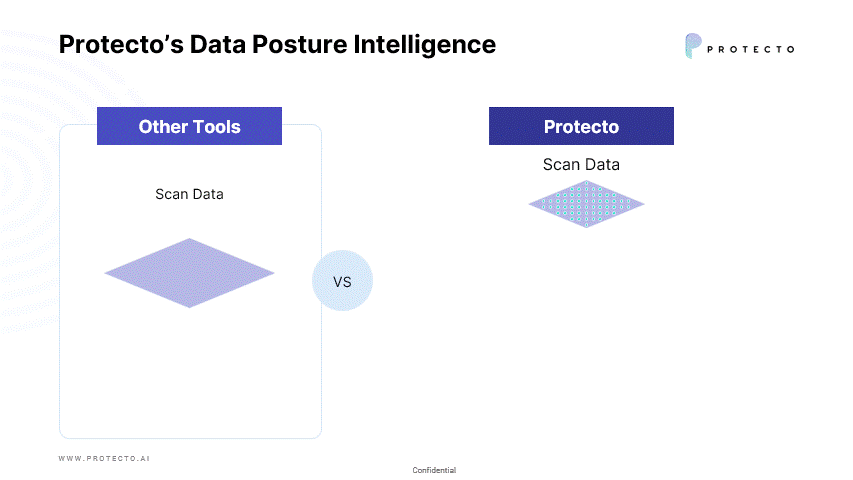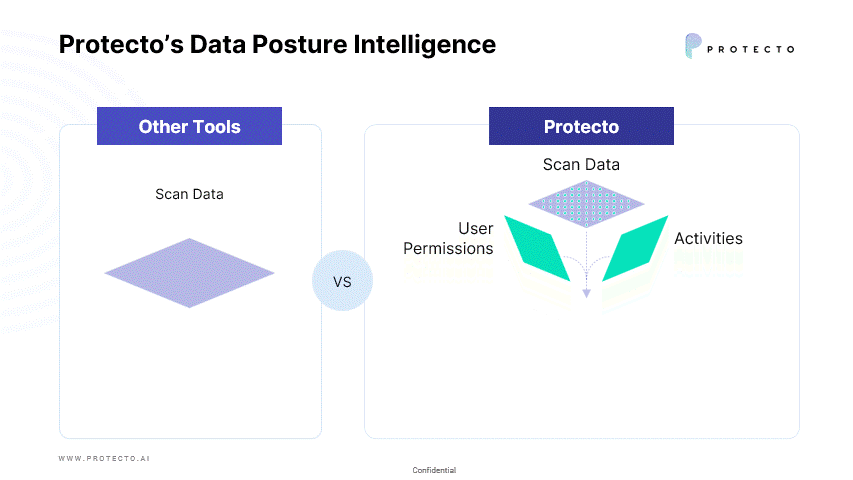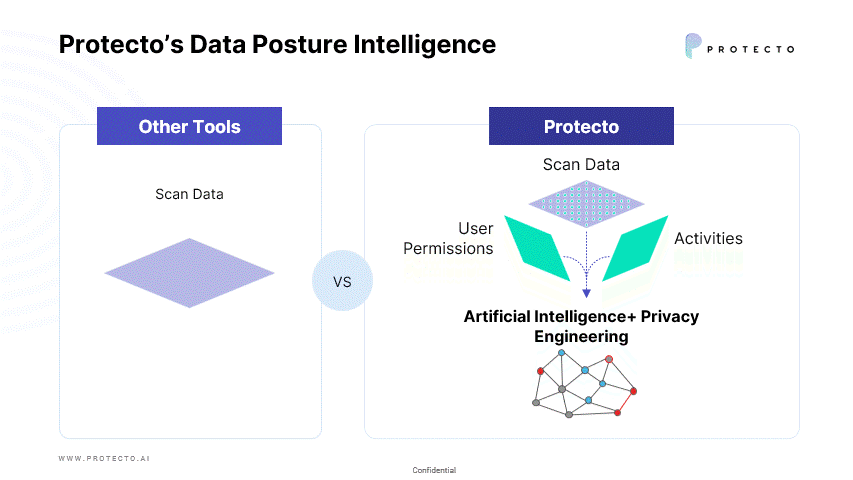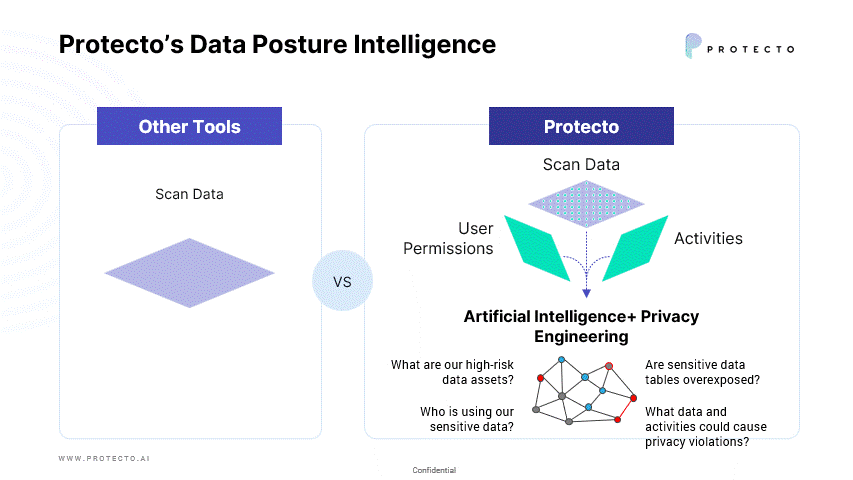
Request a demo to see how Protecto’s Data Posture Intelligence and Intelligent Tokenization can address privacy needs that is not offered by traditional Data Security Posture Management solutions.
FAQs:
1. What is Security Posture Management (SPM)?
Security Posture Management refers to the overall cybersecurity strength and resilience of an organization's IT environment. It involves the continuous assessment and management of security measures, policies, and controls to ensure that they align with the organization's security goals. SPM provides a comprehensive view of an organization's security posture, highlighting vulnerabilities and areas for improvement. It encompasses various aspects, including configuration management, risk assessment, and compliance monitoring.
2. How does Data Security Posture Management (DSPM) work?
Data Security Posture Management (DSPM) focuses specifically on the protection of sensitive data within an organization. It works by continuously monitoring and analyzing the data security controls, configurations, and policies in place. DSPM tools provide real-time visibility into how data is stored, accessed, and shared across an organization's IT infrastructure. By identifying and addressing vulnerabilities and misconfigurations, DSPM helps organizations strengthen their data security posture and comply with data protection regulations.
3. What is the difference between Cloud Security Posture Management (CSPM) and Data Security Posture Management (DSPM)?
While both CSPM and DSPM aim to enhance an organization's overall security posture, they have distinct focuses. CSPM is primarily concerned with securing cloud infrastructure, ensuring that configurations and settings within cloud environments are optimized for security. On the other hand, DSPM specifically concentrates on safeguarding sensitive data, regardless of where it resides – be it on-premises or in the cloud. While there may be some overlap in functionalities, their emphasis sets them apart, with CSPM focusing on broader infrastructure security and DSPM honing in on data-centric security.
4. What is the difference between Data Loss Prevention (DLP) and Data Security Posture Management (DSPM)?
DLP and DSPM are both integral components of a comprehensive data protection strategy, but they serve distinct purposes. DLP primarily focuses on preventing unauthorized access, use, or sharing of sensitive data. It involves monitoring and controlling data in motion, at rest, and in use. In contrast, DSPM is broader, encompassing the overall management of an organization's data security posture. While DLP is more action-oriented, DSPM is concerned with continuously assessing and improving the policies, configurations, and controls related to data security.
5. What are the two types of Data Loss Prevention (DLP)?
There are two primary types of Data Loss Prevention:
- Network DLP: Monitors and controls data in transit over the network, preventing unauthorized data transfer or leakage.
- Endpoint DLP: Focuses on securing data at the endpoint, such as on devices like computers, laptops, or mobile devices. It ensures that sensitive data is protected even when accessed or stored locally on individual devices.
Prevent millions of $ of privacy risks. Learn how.
We take privacy seriously. While we promise not to sell your personal data, we may send product and company updates periodically. You can opt-out or make changes to our communication updates at any time.




