Language models now touch contracts, tickets, CRM notes, recordings, and code. That means personal data, trade secrets, and regulated content move through prompts, embeddings, caches, and third-party endpoints. If your audit still reads like a generic security review, you will miss the places where leaks actually happen. A modern LLM Privacy Audit Framework starts where the risk starts. It inspects unstructured data at ingestion, it enforces access during retrieval, it screens prompts and outputs at inference, and it verifies deletion across vectors and logs.
This article lays out a practical, testable framework you can run every quarter. It focuses on evidence you can show: lineage logs, consent checks, masking coverage, and retention proofs. You will get a step sequence, artifacts to collect, example tests, and metrics to track. Where automation helps, we note how Protecto simplifies the hard parts like discovery, redaction, DLP, and audit packaging.
The Audit Outcome You Actually Need
By the end of an LLM privacy audit you should be able to answer, with proof:
- What data did we touch. Source systems, sensitivity classes, regions, and owners.
- Why we touched it. Lawful basis, purpose codes, and consent status at the time of processing.
- How we protected it. Masking at ingestion, access-controlled retrieval, inference DLP, and role-aware routing.
- Where it traveled. Models, vendors, regions, caches, and embeddings with timestamps.
- When it was deleted. Retention clocks, DSAR handling, and deletion receipts for raw and derived stores.
- What went wrong and how fast we fixed it. Incident logs, MTTR, and mitigations.
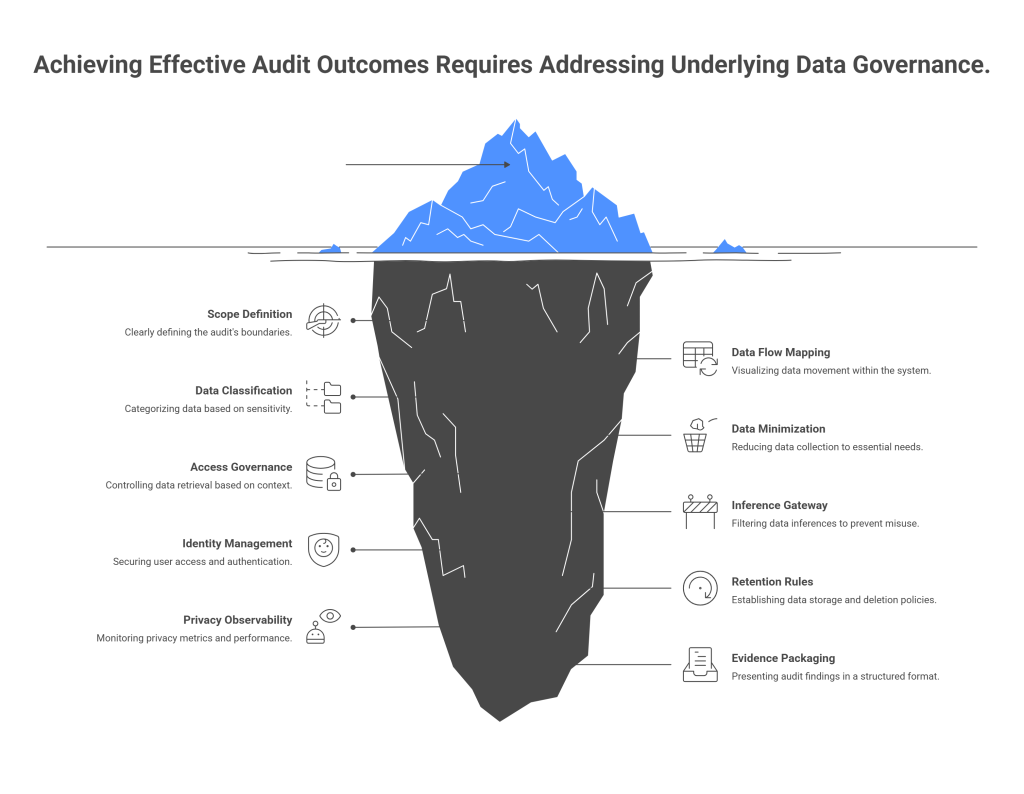
Step 1: Fix the Scope Before You Fix the System
Start by defining the scope that auditors will inspect. Be specific.
- Use cases in scope: ticket summarization, email drafting, contract review, knowledge search, code assistant.
- Models and endpoints: managed APIs, private deployments, fine-tuned variants, and any agent frameworks.
- Data classes: PII, PHI, PCI, customer communications, employee data, financial forecasts, source code.
- Regions and units: where data originates and where it may be processed.
- Vendors: model providers, vector databases, labeling partners, analytics, and observability platforms.
Step 2: Draw the Data Flow With Enough Detail to Matter
A privacy diagram that shows boxes and arrows is not enough. You need the flows that audits will test.
- Where raw files arrive. How they are parsed. What metadata survives.
- Where redaction or tokenization runs. Which patterns are removed.
- Where embeddings are generated and stored. What tags and ACLs are attached.
- How retrieval works. Which filters run before and after similarity search.
- How prompts are built. Which context is injected and by whom.
- How outputs are screened and logged. Where lineage is written.
- Where caches and analytics land. How long they live.
Treat this like infrastructure as code. Keep the diagram and a machine-readable map in your repo. Protecto can generate a data lineage graph from observed flows, which saves weeks of interviews.
Step 3: Classify Data and Assign Purpose Codes
Auditors look for purpose limitation and data minimization. Make both visible.
- Tag every source and every chunk with sensitivity (PII, PHI, PCI, IP, code) and purpose (training, retrieval, analytics, or none).
- Attach lawful basis and consent status where consent is relevant.
- Encode region and owner attributes for retrieval filtering and residency checks.
Your retrieval layer must use these tags at query time. If a user in Region A searches, chunks tagged Region B should not even be candidates. If the purpose is “support,” chunks tagged “legal” should be excluded. Protecto applies tags at ingestion and enforces them at retrieval and inference.
Step 4: Make Minimization Non-Negotiable at Ingestion
Audits fail when models see secrets and identifiers they did not need. Remove them before any model call.
- Redact names, emails, phone numbers, card numbers, API keys, access tokens, and GPS coordinates.
- Tokenize identifiers you will need later, then store the mapping in a secure vault with strict access.
- Strip document headers and hidden metadata like tracked changes, author fields, and EXIF tags.
- Normalize formats so parsers cannot skip sections.
Run redaction as a gate, not as an optional job. Block ingestion that fails masking rules. Protecto can detect PII, PHI, PCI, and secrets across text, PDFs, spreadsheets, and images, then mask or tokenize before vectorization.
Step 5: Govern Retrieval With Access, Residency, and Context
Most leakage happens in retrieval-augmented generation. Fix the retrieval path.
- Enforce ACL filters before similarity search returns candidates.
- Keep per-region indices where needed. Do not mix documents across legal boundaries.
- Prefer least-sensitive tie breaks. When two chunks match equally, return the safer option.
- Log retrieval provenance: which documents were eligible, which were fetched, which were quoted.
If your RAG stack cannot apply these controls, put a gateway in front of it. Protecto can block out-of-scope retrievals, apply region and role filters, and record provenance for audits.
Audit artifact: “Retrieval Policy” plus sample logs showing denied candidates, selected chunks, and reason codes.
Step 6: Route Inference Through a Gateway That Can Say No
Do not connect apps directly to models. An inference gateway centralizes privacy controls.
- Input screening: detect PII, secrets, and sensitive phrases; block or rewrite risky prompts.
- Role-aware routing: choose public, enterprise, or private endpoints based on data class and region.
- Output filters: scrub identifiers, file paths, and system instructions before the app sees results.
- Prompt-injection defenses: sanitize untrusted content, remove hidden directives, and constrain tools.
- Lineage logging: record who asked, which model answered, what filters fired, and which sources were cited.
This turns your privacy policy into executable checks. Protecto operates as a model-agnostic gateway for screening, routing, and logging.
Step 7: Lock Identity and Access Before You Lock Anything Else
Privacy collapses when access is sloppy.
- Enforce SSO and MFA. Provision with SCIM. Avoid shared accounts.
- Use purpose-bound roles such as support, sales, finance, engineering, and legal.
- Attach purpose codes to sessions so retrieval and inference use them.
- Record who accessed what, when, and for which purpose.
Align roles with the tagging in Steps 3 and 5. If a role cannot legitimately view client names, retrieval should never return a chunk with direct identifiers.
Step 8: Set Retention and Deletion Rules You Can Actually Execute
Deletion is where audits get real. Plan it up front.
- Define retention clocks for raw documents, normalized text, embeddings, caches, and logs.
- Start different clocks at sensible events. A ticket’s raw text may keep for 1 year. Embeddings might keep for 90 days.
- Build DSAR automation that erases raw and derived data.
- Emit deletion receipts with object IDs, stores, timestamps, and policy versions.
Do not forget backups and replicas. Use rolling windows and documented exceptions. Protecto orchestrates multi-store deletion and keeps receipts for audit review.
Step 9: Establish Privacy Observability and KPIs
You cannot improve what you do not measure. Track a small set of indicators that reveal privacy health.
- Sensitive prompt rate and the share masked or blocked
- Retrieval denial rate by reason code, including residency and ACLs
- Redaction coverage by source and element type
- DSAR time to close and deletion success rates
- Incident count and mean time to remediate
- False positive and false negative rates for DLP rules
Publish these in a dashboard for leadership. Protecto aggregates policy hits, lineage, and deletion outcomes across models and vendors so reporting is consistent.
Audit artifact: “Privacy Metrics Report” for the previous quarter with trends and actions taken.
Step 10: Package Evidence Like an Engineer, Not a Lawyer
Auditors want artifacts that match your claims. Assemble an evidence pack that is easy to verify.
Core sections to include:
- Scope Register and Data Flow Map
- Classification Catalog and Tagging Rules
- Masking Coverage Report with samples
- Retrieval Policy and provenance logs
- Inference Gateway Policy, injection defenses, and lineage logs
- Access Control Matrix with SSO, MFA, SCIM proof
- Retention Matrix and Deletion Receipts
- Incident Response Playbook and last quarter’s incident timeline
- Privacy Metrics with ownership and improvement plans
Bundle short README files that explain how to read each artifact. With Protecto, you can export policy configurations, logs, and receipts into a single audit bundle.
Field Tests: What to Actually Run During the Audit
Move beyond interviews. Run live tests.
Masking test: Upload a red-team document containing an email, card number, and API key. Confirm ingestion rejects or masks it, and verify embeddings contain no direct identifiers.
Retrieval test: Ask a user in Region A to query for a document tagged Region B. Verify the document is not a candidate and that the denial appears in logs with a residency reason code.
Inference test: Craft a prompt with a secret in plain text, then inside a screenshot, then inside a PDF. Confirm gateway detection, prompt rewriting or blocking, and an output scrub for any leaked string.
Injection test: Feed a page with hidden “Ignore all rules” text to an agent. Confirm your gateway strips the directive and the agent is limited to allow-listed tools.
Deletion test: Submit a DSAR for a synthetic identity. Confirm raw and derived artifacts, including vectors and caches, are purged. Produce receipts within your SLA.
Consent test: Toggle a user’s training consent from on to off. Verify that new tickets are excluded from training sets and that the change is recorded with timestamp and policy version.
Record screenshots, hashes, and log excerpts for each test. Auditors love repeatability.
Common Pitfalls and How to Avoid Them
- Output-only scrubbing. If you only filter answers, the model already saw the secret. Mask at ingestion, then filter again at output.
- Single shared index. Mixing regions and ownership in one vector store invites violations. Partition or tag strictly and enforce at retrieval.
- Invisible stores. Developers forget embeddings, caches, and analytics tables. Add them to retention and DSAR flows.
- Consent theater. A banner no one reads does not drive runtime decisions. Store consent with scope and version, then check it at ingestion and inference.
- Shadow endpoints. Teams route around the gateway because it is slow or blocky. Tune thresholds, fix false positives, and make the official path faster.
What “Good” Evidence Looks Like
Auditors do not need glossy charts. They need verifiable artifacts.
- A log line that shows blocked retrieval with reason=residency and a region code.
- A vector store query that returns zero hits for a masked email string.
- A deletion receipt listing four object IDs across three stores with UTC timestamps.
- A lineage record linking user, role, model, retrieved chunks, filters fired, and the final hash of the answer.
- A metrics chart that shows sensitive prompt rate dropping after you added client-side masking.
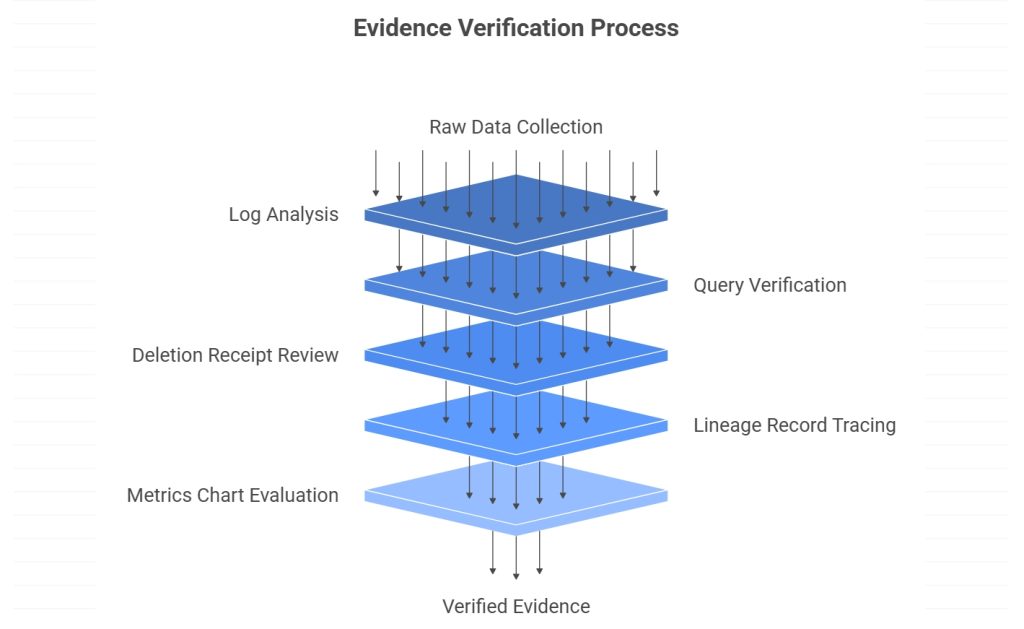
Building the Framework Into Your SDLC
An audit you run once a year is better than nothing. A framework baked into delivery is better than audits. Add checks to CI/CD.
- Pre-ingestion tests that fail builds when masking coverage drops below thresholds.
- Retrieval policy tests that ensure ACL and residency filters run before similarity.
- Gateway policy unit tests for DLP patterns and injection sanitizers.
- Retention tests that simulate DSARs against staging data and verify purges.
- Drift alerts when model routes change or new connectors appear without tags.
Treat privacy tests like load tests. When they fail, block releases. Protecto integrates with pipelines to run masking checks and policy simulations before you ship.
How Protecto Accelerates Your LLM Privacy Audit
If you want the framework without the glue work, Protecto acts as a privacy control plane across your LLM stack:
- Automated discovery and classification across wikis, tickets, file stores, lakes, and code.
- Real-time masking and tokenization at ingestion so embeddings and prompts never carry raw identifiers.
- Policy-aware retrieval and inference that enforces ACLs, residency, consent scope, and DLP before answers are generated.
- Prompt-injection defenses and role-aware routing across public, enterprise, and private endpoints.
- Retention orchestration and DSAR automation with deletion receipts for raw and derived stores, including vectors and caches.
- Audit packaging and dashboards with lineage logs, policy hits, masking coverage, and SLA reports you can hand to auditors.




