Context Security for Agentic AI
Protect Enterprise Data Across Every AI Interaction
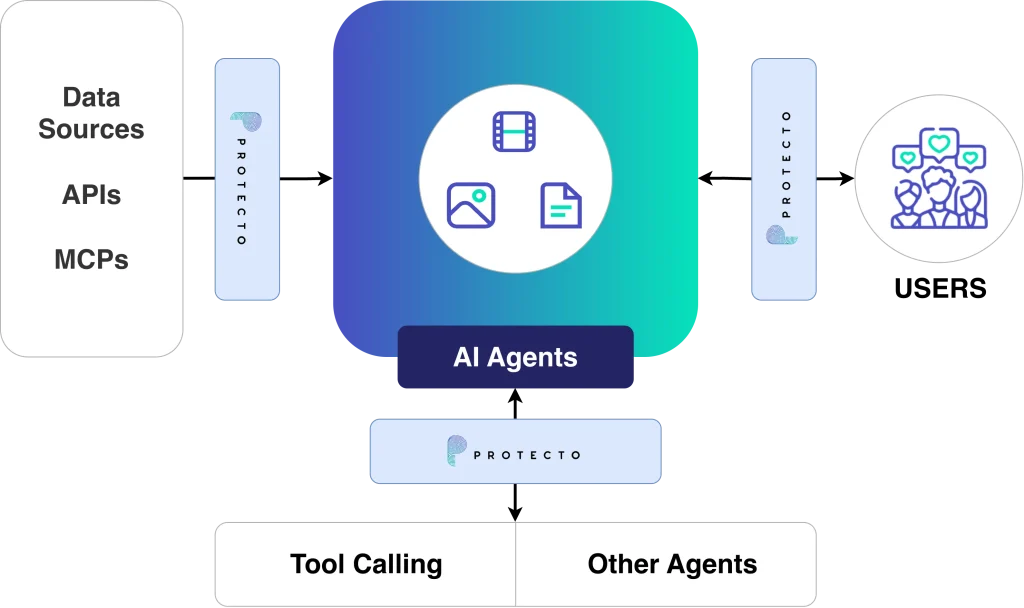
One platform across LLMs, agents, and MCP pipelines. Protecto sits between your enterprise data and every AI system. It detects sensitive information, masks it in real time, enforces who sees what, and logs everything.
- >99.9% Accuracy
- Minutes to integrate
- Multi-language
- HIPAA/GDPR/PDPL
- Trusted by Engineering Teams Building AI at Scale





Sensitive Data Moves With AI Context. Security Should Too
Traditional security draws a perimeter around data: databases, firewalls, structured folders. AI doesn't respect that perimeter. It pulls data from everywhere, rewrites it into prompts, summaries, and agent actions, and sends it across systems. The data changes form. The sensitivity doesn't. Security needs to follow the context, not the perimeter. Context Security.

“Protecto enabled us to deliver data security, privacy, and compliance for our AI features at scale across 3,000+ enterprise clients, strengthening customer trust in our AI automation solutions.”
- 3,000+ companies sensitive data protected
- Over 1M+ AI interactions with zero data breaches
- 3x faster AI adoption rate among regulated industry clients
Why Traditional Controls Fail in the AI Era
Your access controls, DLP rules, RBACs, and compliance models were designed for predictable, fixed data flows. AI broke that assumption.
DLP Wasn't Built for This
AI needs data. DLP gives you two options: block it and break AI, or allow it and lose control. You need a third option.
RBAC stops at the source
You control who queries the database or sees files. You don't control what AI does once data enters the reasoning layer. Your RBAC no longer applies.
Compliance roadblocks
GDPR, HIPAA, PDPL, and DPDP assume you know where data lives and how it's used. AI reads, transforms, and moves data across systems in seconds. Your audit trail goes dark.
The Context Security Platform in Action
A lightweight API layer that plugs into your AI stack. No architectural changes. Production-ready in days.
Tokenize at Ingestion
- PII/PHI Detection
- Context-Preserving
- API Integration
RBAC at Inference
- Role-Based Access
- Real-time Policy
- AD Integration
Prevent Data Leaks
- Zero False Negatives
- Audit Trail
- Compliance Reports
Maintain AI Accuracy
- Semantic Integrity
- Reversible Masking
Context-Based Access Control
Role-based access isn't enough for AI agents. Meet CBAC.
Traditional RBAC was designed for humans clicking through apps. AI agents don't work that way. They call tools, chain actions, and access data in ways no static role can govern. Protecto's Context-Based Access Control (CBAC) makes data access decisions at the moment the agent asks, based on who's asking, why, and what context they're operating in.
Why AI-First Enterprises Choose Protecto
Ship AI faster. Stay compliant. Keep accuracy intact.
Security Without Compromise
Generic redaction destroys context. Protecto’s tokenization preserves semantic meaning. Your LLMs generate accurate responses, even on protected data.
- 99.9% detection accuracy, lowest false negatives
- Format-preserving encryption
- Zero degradation in AI performance
RBAC for AI Agents
Control who sees what at inference time. Sales agents can’t access support data. Analysts see anonymized aggregates. Supervisors unmask when authorized.
- Dynamic masking/unmasking based on permissions
- Integrates with Active Directory, Okta & more
- Complete Audit Trail - Audit who accessed what, why, when, where
Discover & Protect Data
Protecto scans your entire data landscape: prompts, responses, documents, logs. Discovers PII, PHI, and business confidential data without manual tagging.
- 200+ sensitive data types detected
- Custom entity support
- Multi-language support
Proven Compliance and Sovereignty
Stop building compliance infrastructure from scratch. Protecto comes pre-configured with policies, audit trails, and reporting for major regulations. Pass audits faster with zero custom development.
- Pre-built HIPAA, GDPR, PDPL, DPDP policies.
- Audit-Ready from Day One (who, what, when, why)
- Exportable compliance reports (PDF, CSV, JSON)

“Protecto enabled our team to harness the full power of AI and analytics while maintaining strict HIPAA compliance and data privacy.”
- 1,000+ Documents Tested and verified in less than a week
- < 30 Days From implementation to full deployment
- $25M+ Projected customer revenue in 12 months
Leading Enterprises Use Protecto
Real-world deployments protecting sensitive data in AI pipelines
Healthcare & Life Sciences
Leading Insurance Provider used Protecto to enable accurate, efficient claims processing while protecting patient data privacy.
- HIPAA-compliant AI assistants
- PHI detection in clinical notes
- Privacy-preserving RAG for patient data
Full compliance and data protection for PHI masking.
Read Case Study
Data Sovereignty for Banks
A leading Middle East bank used Protecto to deploy Gemini under strict PDPL laws.
- 100% PDPL compliance achieved
- Deployed in 3 weeks
- Zero data egress to public cloud
99%+ detection accuracy and full compliance.
Read Case Study
Access Control for Multi-Agent AI
A global enterprise integrated Protecto to manage data access across multi-agent workflows.
- Real-time RBAC for AI agents
- Multi-tenant security policies
- Centralized access control layer
Secure collaboration across 50,000+ users.
Read Case Study
The Build vs. Buy Analysis Your CTO/CISO Needs
Save 18 months and $500K+ by licensing instead of building. Here's what the math actually looks like.
| Features | Protecto | Generic Tools | DIY Solution |
| Time to Production | < 1 week | 3-6 months | 6-18 months |
| PII/PHI Accuracy | 99.9% | 92-95% | 85-90% |
| Context Preservation (AI accuracy intact) | ✓ | ✕ | ✕ |
| Multilingual support | ✓ 50+ languages | ✕ | ✕ |
| Real-Time RBAC | ✓ | Partial | ✕ |
| Multi-Tenancy | ✓ | Limited | ✕ |
| On-Premises Option | ✓ | ✕ | ✓ |
| Auto-Scaling | ✓ | ✓ | ✕ |
| Compliance Reporting | ✓ | Basic | ✕ |
| Context Based Access Control (CBAC) | ✓ | ✕ | ✕ |
Key Features
Core capabilities that make Protecto the most advanced AI data security platform
Sensitive Data Detection
Automatically detect PII, PHI, and confidential enterprise data across prompts, documents, and AI outputs.
Context-Based Access Control
Control who can see what information during AI interactions based on identity, role, and context.
Privacy-Preserving Tokenization
Protect sensitive values while preserving semantic meaning so AI models maintain accuracy.
Secure RAG & Agent Workflows
Protect data flowing through RAG pipelines, MCP tools, and multi-agent systems.
Policy-Driven Governance
Define policies once and enforce them automatically across AI prompts, responses, and workflows.
Enterprise Compliance
Built-in support for regulations like HIPAA, GDPR, PDPL, and DPDP with full audit trails.
AI Stack Integration
Integrates with LLM platforms, orchestration frameworks, vector databases, and model gateways.
Flexible Deployment
Run Protecto in SaaS, private VPC, or fully on-prem environments.
Multi-Tenant Security
Securely isolate teams, customers, and environments with independent policies and controls.
Full Auditability
Track exactly who saw what, and when.
Integrate Anywhere in Your AI Stack
RESTful APIs | Python SDK | Deploy in 3 ways.
Compatible With






AI Changed the Game. Context Security Is the Answer.
Protecto gives you full control over the data layer that powers GenAI - without breaking performance or accuracy.
- SOC2 Certified
- HIPAA Compliant
- GDPR Ready
- ISO 27001