AI Data Security for Gen-AI and SaaS Platforms
Protect Sensitive Data in Gen-AI Applications
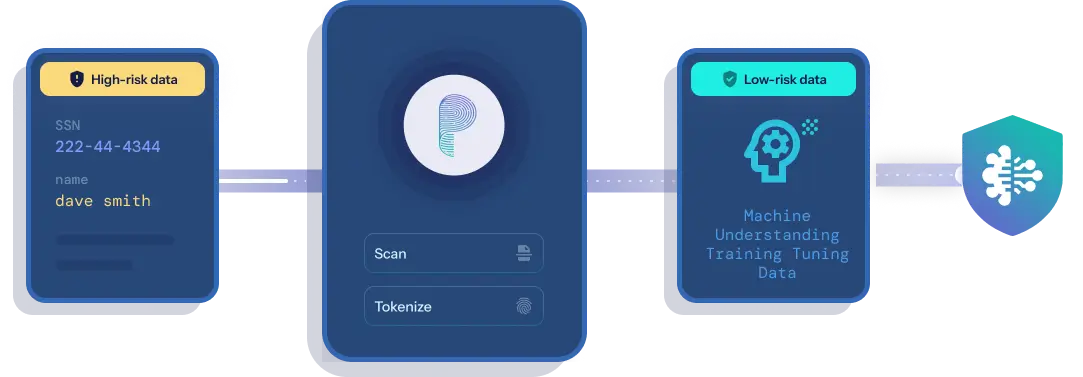
Protecto delivers AI data security by intelligently identifying and masking sensitive information, enabling safe, compliant, and privacy-first adoption of GenAI and SaaS applications.
- Trusted by Engineering Teams Building AI at Scale





AI Data Security Challenges Enterprises Can’t Ignore
As organizations accelerate their use of GenAI and SaaS platforms, they face new security threats and compliance hurdles. Traditional data protection methods are inadequate for the scale, complexity, and sensitivity of AI-driven workflows.
- Sensitive data hidden in unstructured inputs
- Growing pressure to meet global compliance
- Redaction breaks context and model accuracy
- No visibility into GenAI data pipelines
- Legacy tools can’t scale across AI use cases
How Protecto Solves AI Data Security at Scale
Protecto’s AI-driven platform is purpose-built to secure GenAI and SaaS workflows. It intelligently discovers and masks sensitive data—preserving utility while ensuring compliance and performance.
Smart Data Detection
- Automatically identifies PII, PHI, and confidential data
- Scans structured and unstructured inputs
- Adapts to custom patterns and formats
Context-Preserving Masking
- Retains meaning and format for accurate AI results
- Works seamlessly with GenAI, LLMs, and RAG models
- Enables privacy without breaking functionality
Compliance & Control
- Aligns with GDPR, HIPAA, DPDP, and more
- Supports role-based access and audit logs
- Fits SaaS, cloud, and on-prem deployments
Trusted by Industry Leaders
Protecto is trusted by over 3,000 companies, including industry leaders like Inovalon, Automation Anywhere, Ivanti, and Nokia. Our solutions have empowered these organizations to integrate AI technologies securely and compliantly.




Built for Enterprise. Optimized for Scale.
On-Premises or SaaS
Deploy Protecto on your servers or consume it as SaaS. Either way, get the full benefits including multitenancy.
Simple APIs
Use sync and async APIs to integrate with any part: preprocessing, context data, prompt, or response.
Auto-scale
Protecto's architecture scales to process billions of rows or runs lightweight on-edge devices, offering versatility and efficiency.
features
Optimized Data Guardrails for Gen-AI
Tailor-made AI data protection for your Gen AI applications

AI Powered Sensitive Data Scanning
Utilize our cutting-edge AI models for robust and accurate identification of PII and other sensitive data.

Custom Pattern Identification
Define and identify unique data patterns specific to your business needs for better data protection.

Accuracy Preserving Data Masking
Apply various data masking techniques tailored to your specific security and privacy requirements.

Entropy-based Tokenization
Securely tokenize sensitive data using entropy-based methods like Anonymization and Pseudonymization, safeguarding privacy while enabling some analytics

Attribute & Role-Based Controls
Implement granular access controls based on user roles and data attributes to enhance security.

Flexible API Options
Integrate data protection features seamlessly into your existing systems with Turnkey API options.

Audit Trails & Reports
Get audit reports on scan, mask, and unmask activities. Helps to meet your compliance needs.

Safety Checks
Achieve seamless compliance with GDPR, HIPAA, and other regulations

Denied keywords
Achieve seamless compliance with GDPR, HIPAA, and other regulations
Get Started with AI Data Security Today
Protect sensitive data in your GenAI and SaaS workflows with Protecto’s AI-powered privacy and compliance platform—request a demo now.
FAQs
What is AI data security?
AI data security refers to protecting sensitive information processed by artificial intelligence systems. This includes preventing data leaks, ensuring privacy compliance, and safeguarding PII/PHI across AI workflows like GenAI and SaaS platforms.
How does Protecto deliver AI data security?
Protecto uses AI-powered detection and masking to secure sensitive data before it enters GenAI, LLM, or SaaS systems—preserving utility while ensuring compliance with regulations like GDPR, HIPAA, and DPDP.
Can Protecto help with data privacy compliance?
Yes. Protecto automates privacy controls and provides tools to meet global regulations including GDPR, HIPAA, CCPA, and India’s DPDP Act—helping enterprises avoid fines and maintain user trust.
Does Protecto support RAG and LLM pipelines?
Absolutely. Protecto integrates directly with Retrieval-Augmented Generation (RAG) systems, LLM agents, and AI platforms to secure data at every step—prompts, context, responses, and logs.
What makes Protecto different from traditional masking tools?
Unlike generic redaction tools, Protecto preserves the context and format of data. This ensures high AI model accuracy while still protecting sensitive information.