Data theft is a serious issue that adversely affects organizations worldwide. Despite enforcing data safety practices, organizations often fall victim to data theft attacks with disastrous, far-reaching consequences. This article will discuss the potential fallout of data theft and how you can prevent data theft in your organization.
What is Data Theft?
Data theft is the illegal or unauthorized transfer or storage of any legally confidential, personal, or financial information. This can include passwords, software code, algorithms, proprietary process-oriented information, or technologies. Data theft can originate inside and outside an organization and can be a significant risk for businesses of all sizes.
You might get the impression that data theft is always based on malicious intent, but this is not always the case. Data theft can also be unintentional. For example, an employee may take home sensitive information on an unsecured drive or retain access to the information after their contract has ended.
Data theft often happens when bad actors aim to sell or exploit the information for identity theft purposes. Data theft occurs when someone gains unauthorized access to someone’s personal information. This information can then be used to access secure accounts, open credit cards, or use the victim’s identity for personal gain.
Despite the term ‘theft,’ the attacker does not take information away from the victim but rather duplicates it for their own use.
Interesting read: Impact Of Regulatory Compliance Laws On Data Privacy & Security
Demystifying data theft: How it happens
Data theft can originate both inside and outside an organization. It can be a result of malicious intent or an unintentional act. For example, an employee may take home information on an unsecured flash drive or retain data access after their contract ends.
There are numerous ways in which data can be stolen. The most common methods are social engineering, weak passwords, and system vulnerabilities. Social engineering involves attackers manipulating individuals to give away confidential information. Phishing is the most widespread form of social engineering, where attackers pretend to be trustworthy sources to trick victims into opening emails, text messages, or instant messages.
Using weak passwords or the same password for multiple accounts can make it easier for attackers to gain access to your data. Furthermore, writing passwords down on paper or sharing them with others is not a secure practice and can lead to data theft.
In addition, hackers can take advantage of system vulnerabilities caused by poorly designed or implemented software applications and network systems. It is important to keep your antivirus software up to date to prevent potential vulnerabilities.
What are the consequences of data theft in an organization?
The consequences of data theft for an organization can be severe and long-lasting. Businesses experiencing data theft can also fall victim to ransomware demands from attackers, steep recovery costs, reputational damage, customer attrition, lawsuits from customers whose data was exposed, and downtime while data is recovered.
Corporate data theft is primarily motivated by financial gain and has caused at least 86% of breaches. Attackers exploit a company’s security vulnerabilities to steal data and sell it to other bad actors. The financial cost and reputational damage of data breaches can be devastating for businesses. In 2018, the average data breach cost was more than $1.2 million, a 24% increase from the previous year. Smaller organizations that lack resources to respond to and recover from data theft are at particular risk, as 60% of small businesses that suffer an attack tend to go out of business within six months.
The impact of data theft goes beyond the immediate financial loss, as existing customers may churn, and it may also lead to a loss of reputation. It can be difficult for brands with a track record of breaches to attract new business. Additionally, companies that mishandle data are exposed to legal action from affected users.
8 ways to prevent data theft in your organization
To prevent data theft, companies must restrict access to their most vital data and resources, keep an eye on all data-related activities performed by their workers, and implement cybersecurity policies that come with clear repercussions for any violations. Here are eight ways to prevent data theft in your organization:
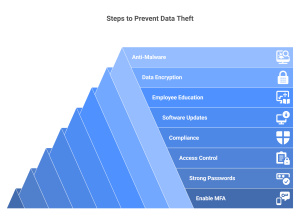
1. Enable Multi-factor Authentication
Adding an extra layer of security, multi-factor authentication makes it mandatory for users to provide two or more forms of identification steps before accessing sensitive information. These forms of identification can include a password, a security token, or a fingerprint. By requiring multiple forms of identification, multi-factor authentication significantly decreases the chances of attackers accessing sensitive information.
2. Implement Strong Password Policies
Implement robust password policies that require users to create complex passwords that are difficult for intruders to guess. Educate employees on the importance of using unique passwords for each account and not sharing them with others. Passwords should be at least eight characters long and ideally include a combination of uppercase and lowercase letters, numbers, and special characters.
3. Enforce Access Control and Authorization
Limit access to sensitive data to only those who need it to perform their duties. Regularly review and update access controls to ensure only authorized personnel can access sensitive information. Use role-based access controls to restrict access based on job function.
4. Ensure Compliance with Data Protection Regulations
Ensures that your organization is compliant with all relevant data protection regulations. This can help prevent data breaches and possibly minimize the damage if one does occur. Regulations such as the General Data Protection Regulation (GDPR) and the California Consumer Privacy Act (CCPA) impose strict requirements on how organizations collect, store, and use personal data.
5. Ensure Periodic Patching and Updating Software
Regularly patch and update all software applications and network systems to fix any vulnerabilities that hackers could exploit. Software vulnerabilities can provide an entry point for attackers to gain access to sensitive data. By keeping software up-to-date, organizations can reduce the risk of data theft.
6. Promote Employee Education and Awareness
Educate employees on the vital importance of data security and their role in preventing data theft. Provide regular training on identifying and avoiding common threats such as phishing attacks. Employees should also be trained on how to handle sensitive data and how to report any suspicious activity.
7. Use Data Tokenization or Encryption
Tokenize or encrypt (as your situation demands) sensitive data, both at rest and also in transit to prevent unauthorized access. Data encryption uses mathematical algorithms to scramble data so it is only readable with the proper decryption key. By encrypting or tokenizing data, organizations can ensure that even if data is stolen, it will be useless to attackers without the decryption key.
8. Implement Strong Anti-Malware Solutions
Use strong anti-malware solutions to protect against viruses, spyware, and other malicious software that can potentially be used to steal data. Anti-malware solutions should be kept up-to-date with the latest virus definitions to ensure maximum protection against new threats.
What should you do in case of data theft?
If your organization becomes a victim of data theft, it is vital to act quickly to minimize the damage. Here are some steps you can take:

- Secure your operations: It’s important to act fast and secure your systems if you suspect a breach. Take affected equipment offline but wait for forensic experts before turning off any machines. Keep a close eye on all entry and exit points, especially those known to have been involved in the breach.
- Involve experts: In order to efficiently handle the situation, it is recommended that a team of experts be assembled. The experts should include individuals from various areas such as forensics, legal, information security, operations, information technology, human resources, communications, investor relations, and management. The size and nature of the company will determine the specific needs of the team.
- Hire a data forensics team: To identify the cause and extent of the security breach, it may be wise to hire impartial forensic investigators. These experts can obtain forensic snapshots of impacted systems, gather and scrutinize evidence, and provide recommendations for resolving the issue.
- Consult with legal counsel: Consult with legal counsel to determine your obligations under federal and state laws. You may need to notify affected individuals, regulators, and law enforcement agencies about the breach.
- Notify affected individuals: If personal data was compromised in the breach, notify affected individuals immediately. Provide them with information about what happened and what steps they can take to protect themselves.
- Report the breach: Report the data theft to law enforcement agencies and other relevant authorities. You can report cases of identity theft directly to the Federal Trade Commission (FTC) in the United States.
- Determine privacy risks: Understanding where the sensitive data lies within the organization’s tech stack is one of the first things that the privacy team must undertake. This includes what types of sensitive data exist in the tech stack, which sources hold that data, which data sources or tables are most at risk, which users have excessive access to sensitive data, how the sensitive data is used, and more.
- Determine best ways to protect sensitive data: Once the sensitive or personal data is uncovered by implementing sensitive data discovery and classification tools, then it is important to protect that data via one of several approaches including masking, encryption, tokenization or redaction, depending on whether/how that data will be used in the future.
By taking these steps, you can help minimize the damage caused by data theft and begin the recovery process.
Suggested read: What Is Data Sprawl & How To Prevent Them
The legal implications associated with data theft
Data theft can have profound legal implications for organizations. If your company has fallen victim to a breach, you will likely face an investigation by regulatory bodies and law enforcement. They will seek to determine what caused the violation, the identities of the perpetrators, and your level of liability.
You may also face litigation from regulatory bodies, customers, clients, or business partners. Depending on the type of data involved and the jurisdiction in which you operate, you may be required to notify affected individuals and regulators about the breach. You may also be subject to fines and penalties for failing to protect personal data adequately.
In addition to regulatory fines and penalties, organizations are also open to civil lawsuits from affected individuals seeking compensation for damages caused by data theft. This can include financial losses, emotional distress, and harm to reputation.
To minimize the legal risks associated with data theft, organizations must implement strong data security measures and comply with all relevant data protection regulations. In the event of a breach, organizations should act quickly to secure their systems, notify affected individuals and regulators, and cooperate with law enforcement investigations.
How Protecto can help prevent data theft in your organization
Data theft is a serious issue that can have far-reaching consequences for organizations. Companies need to take proactive measures to prevent data theft and to have a plan in place to respond quickly and effectively in the event of a breach. By implementing strong data security measures, educating employees, and complying with relevant regulations, organizations can reduce the risk of data theft and minimize the damage if a breach does occur. Companies must remain vigilant and continuously assess and improve their data security practices to protect against this ever-evolving threat.
Protecting against data theft can become much easier with the help of Protecto. Our platform offers a complete data privacy and security framework that can take care of all your privacy and compliance requirements for structured data. Get in touch with us today to see how our platform makes your privacy and compliance effortless or request a free trial.



