AI agents are rapidly moving from experimentation into production across finance, healthcare, enterprise IT, and critical infrastructure. Unlike traditional applications, agents plan, reason, delegate, and act autonomously across systems and data sources. This expanded autonomy dramatically increases the security blast radius.
To address this shift, OWASP released the OWASP Top 10 for Agentic Applications (2026) as part of the OWASP GenAI Security Project. The report identifies the most critical risks unique to agentic systems, including goal hijacking, privilege abuse, memory poisoning, insecure inter-agent communication, and rogue agent behavior. A recurring theme across the report is clear: uncontrolled access to data and context is the primary failure mode in real-world agent deployments . https://genai.owasp.org/resource/owasp-top-10-for-agentic-applications-for-2026/
This is where Protecto focuses.
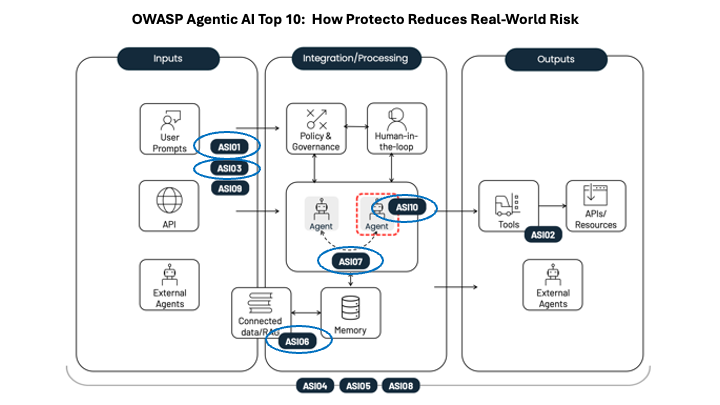
Below are the OWASP Agentic risks that Protecto and Context-Based Access Control (CBAC) directly mitigate.
ASI01 – Agent Goal Hijack (via Data and Context)
OWASP explains that agents cannot reliably distinguish instructions from content. Malicious instructions embedded in documents, emails, or retrieved data can silently redirect agent behavior without user interaction.
Protecto mitigates this by enforcing policy at the data layer. Sensitive or high-risk content is detected and controlled before it enters the agent’s reasoning loop. By limiting what context the agent can see and act on, Protecto reduces the impact of indirect prompt injection and goal hijacking through untrusted data.
ASI03 – Identity and Privilege Abuse
OWASP highlights that agents often inherit excessive privileges through delegation chains, cached credentials, or over-broad access scopes, making least privilege nearly impossible with traditional RBAC.
Protecto’s Context-Based Access Control enforces least privilege at inference time. The same agent and same prompt produce different outputs depending on the user’s role, intent, and policy. Sensitive data is only exposed when explicitly allowed, preventing accidental overexposure through agent delegation.
ASI06 – Memory and Context Poisoning
Agentic systems rely on persistent memory such as summaries, embeddings, and RAG stores. OWASP warns that poisoned or corrupted context can persist across sessions and influence future decisions.
Protecto prevents sensitive data from being blindly written into agent memory. Data is classified and tokenized before storage, ensuring long-term memory does not become a vector for persistent leakage or contextual corruption.
ASI07 – Insecure Inter-Agent Communication (Data Exposure)
OWASP documents how data leaks can occur when agents exchange messages or share context without consistent authorization controls.
Protecto applies uniform data policies across agent-to-agent workflows and MCP-style integrations. Sensitive context remains protected as it moves between agents, tools, and downstream systems.
ASI10 – Rogue Agents (Data Leakage and Compliance Impact)
OWASP defines rogue agents as agents that gradually deviate while appearing compliant, leading to silent data exposure and policy violations.
Protecto limits the damage a rogue agent can cause by ensuring sensitive data is never exposed without policy approval. Every access decision is logged, enabling auditability, detection, and enforcement of compliance.
Why This Matters
The OWASP report makes one thing clear: most agentic AI failures are not model failures. They are control failures.
OWASP defines the risks. Protecto solves the ones that block enterprise adoption: uncontrolled data exposure, over-privileged agents, poisoned context, and lack of auditability.
Context-Based Access Control is not optional for production agents. It is the control plane that makes agentic AI safe to deploy at enterprise scale.
Protect what your AI runs on.




