Data security is a critical concern for organizations worldwide. Cyberattacks and data breaches have put sensitive information such as customer data, payment details, and user credentials at constant risk. Techniques like tokenization vs hashing provide essential tools to safeguard this information effectively.
Understanding the distinctions between these methods is crucial for selecting the right approach. Tokenization and hashing each offer unique strengths, serving different purposes in data security strategies. This guide explores their definitions, differences, and practical applications, helping businesses implement robust protection measures that align with industry regulations and operational needs.
What Is Tokenization?
Tokenization is a process that replaces sensitive data with randomly generated tokens. These tokens hold no intrinsic value and are meaningless outside the secure system where they are used. This method ensures that sensitive information remains protected even if the tokens are intercepted.
How Tokenization Works
- Original data is replaced with a randomly generated token.
- A secure token vault stores the mapping between the token and the original data.
- Only authorized systems can retrieve the original data when needed, ensuring secure access.
Tokenization minimizes exposure to sensitive information by restricting its availability to authorized users. This makes it a preferred choice for industries requiring high data security and compliance levels.
Key Use Cases of Tokenization
- Payment Processing: Secures credit card numbers and other payment details during transactions, ensuring compliance with PCI DSS.
- Healthcare: Protects PII and PHI, meeting HIPAA requirements for data privacy.
- E-commerce: Safeguards customer payment details during online purchases, preventing unauthorized access.
- Customer Data Protection: Ensures sensitive personal information remains secure in CRM systems and other databases.
- Fraud Prevention: Reduces the risk of fraud by replacing valuable data with tokens with no exploitable value.
- Cloud Data Security: Protects sensitive information stored in cloud environments by replacing it with secure tokens.
What Is Hashing?
Hashing converts data into a fixed-length string using a mathematical algorithm. The output, called a hash, is unique to the input data and cannot be reversed to its original form. This makes hashing an effective tool for verifying data integrity and securing sensitive information like passwords.
How Hashing Works
- Data is passed through a hash function.
- The function generates a unique hash value for the input.
- Any alteration to the input produces an entirely different hash, enabling verification of data integrity.
Hashes are deterministic, meaning the same input will always produce the same hash. This property is essential for tasks like password verification and data integrity checks.
Key Use Cases of Hashing
- Password Storage: Secures user passwords by storing their hashes instead of plaintext, adding a layer of protection.
- Data Integrity Verification: Ensures that files or messages remain unchanged during transmission, identifying tampering attempts.
- Digital Signatures: Validates the authenticity of electronic documents, ensuring they have not been altered.
- Blockchain Technology: This technology uses hashing to link blocks securely and maintain data integrity.
- File Authentication: Confirms that downloaded files match their original versions.
Tokenization Vs Hashing: Key Differences

Reversibility
- Tokenization: Reversible through access to a secure token vault.
- Hashing: Irreversible, ensuring that the original data cannot be reconstructed.
Purpose
- Tokenization: Designed to protect sensitive data in live systems and transactional environments.
- Hashing: Focused on verifying data integrity and securing static information like passwords.
Security Features
- Tokenization: Relies on controlled access to the token vault for security.
- Hashing: Uses one-way encryption, ensuring data cannot be retrieved from the hash.
Performance
- Tokenization: Requires additional storage and processing for the token vault, impacting performance in large-scale systems.
- Hashing: Lightweight and computationally efficient, making it ideal for high-speed operations.
Compliance and Regulation
- Tokenization: Aligns with PCI DSS and HIPAA, reducing compliance scope by securing sensitive data.
- Hashing: Supports regulatory requirements for data integrity but is less applicable for live data protection.
Tokenization Vs Encryption
Encryption transforms data into ciphertext using a key. Unlike tokenization, encryption allows the original data to be decrypted back to its original form.
When to Use Encryption
- Securing data in transit across networks.
- Protecting sensitive information stored in databases.
- Ensuring compliance with regulations like GDPR and CCPA.
Encryption complements tokenization by securing data that requires frequent access while maintaining confidentiality. It is particularly effective for protecting sensitive communications and stored information.
Interested Read: Format-Preserving Encryption vs Tokenization: Learn the Key Differences
Encryption Vs Tokenization Vs Masking
Each method serves distinct purposes in data security:
- Encryption: Protects data during transmission and storage, ensuring confidentiality.
- Tokenization: Secures live data by replacing it with tokens, reducing the scope of compliance requirements.
- Masking: Anonymizes data for non-production environments, such as testing and training systems.
Combining these techniques creates a comprehensive data security strategy that addresses various risks and compliance needs. Organizations often use encryption for communication, tokenization for transactional systems, and masking for development environments.
Interested Read: Data Masking Vs Tokenization: Key Differences and Use Cases
Which Is Better for Your Data Security?
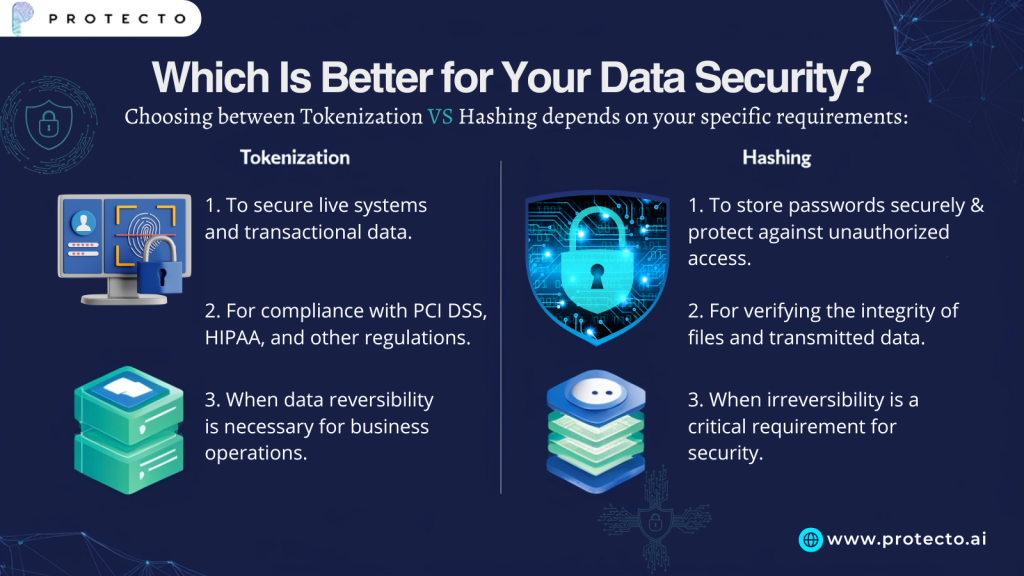
Choosing between tokenization and hashing depends on your specific requirements:
Use Tokenization:
- To secure live systems and transactional data.
- This is for compliance with PCI DSS, HIPAA, and other regulations.
- When data reversibility is necessary for business operations.
Use Hashing:
- To store passwords securely and protect against unauthorized access.
- For verifying the integrity of files and transmitted data.
- When irreversibility is a critical requirement for security.
Both methods can enhance data security when applied appropriately. Organizations should evaluate their data types, operational needs, and compliance requirements to determine the best approach. Combining tokenization, hashing, and complementary methods like encryption can provide a robust security framework.
Conclusion
Tokenization and hashing are indispensable tools in modern data security. Each technique offers unique advantages, addressing different aspects of data protection. By understanding their differences and practical applications, businesses can implement effective strategies to safeguard sensitive information and comply with regulatory standards.
Combining tokenization, hashing, and complementary methods like encryption and masking ensures a robust security framework. This layered approach provides comprehensive protection against data breaches, instills customer trust, and supports long-term business success in an increasingly digital world. Organizations that adopt these strategies and invest in resources like Protecto position themselves as leaders in secure data management, meeting the demands of a data-driven economy.



