Large Language Models: Usage and Data Protection Guide
Amar Kanagaraj
June 21, 2023

Large Language Models (LLMs), like GPT-4 by OpenAI, have various applications, spanning from interactive public models to privately hosted instances for businesses. Each application brings forth its unique data protection and privacy compliance concerns. This write-up explores different methods of leveraging LLMs and each scenario's related data protection considerations.
What is LLM Security?
When data is stored in LLMs, the question comes regarding their ability to store data. LLM Data Security has been scrutinised for the past few years or so due to the explosion of using Generative AI in the past few years. LLM security is the process of using LLM in Data Privacy methods. You can use LLM’s high processing power for the benefit of cybersecurity.
Protecto provides top-notch security with its tokenization solutions such that you can reliably use ChatGPT, Gemini and other LLMs without the fear of losing data. Experience the full roster of benefits of Generative AI without compromising your privacy or security in cyberspace.

But why use LLM in data privacy? Isn’t the computational resources too high making it time-consuming? Many companies prefer accuracy over computational time in the grand scheme of things. Hence, using LLM for data security is at the forefront for various purposes.
Benefits of LLM Security
There are many benefits of LLM Security being used in your enterprise. Some of them are:
High Processing Power
As we know, LLMs are extremely large Machine Learning models able to perform Big Data Analytics. These models have high amounts of processing powers with which they can check every nook and cranny of your enterprise with their LLM Data Security parameters.
Custom-built functions
When it comes to LLM Data Protection, instead of using user-defined functions to analyze data, LLMs can be used to go through raw, unstructured data and create their custom functions. This improves LLM Data Privacy because most LLMs are black boxes; which means we can’t exactly tell what’s happening during the processing.
Many Parameters for processing
Unlike the traditional Deep Neural Networks or other Machine Learning models, LLMs can process through a lot more parameters than humanely possible. For scale, the GPT-4 LLM is trained using 1.3 billion parameters. This amount of parameters improves the LLM Data Protection standards by a lot.
Protecto guarantees data privacy LLM capabilities by using LLMs to generate synthetic data which, even though is derived from the original data, is completely anonymised and has little to no relation with the real data. This data can be curated to perform data analysis without the need to use real data.
Now we know why using LLMs is beneficial. Data Privacy LLM techniques are used in various Data Security applications. But, what are they?
Top 10 LLMs Data Security Applications
There are many real-world applications implementing LLM Data Security techniques. Here are the top 10 use cases.
Poisoning of Training Data
In LLM Data Protection, the process starts from the type of data it is trained with. If malicious users find out about the training dataset, they can identify the key features through advanced data analysis techniques and then populate the data with false positives dragging down the model’s accuracy. LLMs can be trained to detect and solve such deceits.
Protecto ensures your data protection by tokenising it in the cloud. Their agentless solution uses LLM techniques to tokenise data, improving cloud security.

Prompt Injections
One of the biggest problems faced by LLMs is their susceptibility to prompt engineering. Using carefully worded prompts, they can make LLMs potentially divulge private information of other users. This causes a great hamper to the concept of using LLM in Data Privacy. But, with granular access and proper parameter tuning in LLMs, they can serve as bastions against prompt injections.
Poor Handling of the Output
Sometimes, while analysing large swathes of data, some outputs may not be validated properly and may be stuck in limbo. Malicious users can make use of this vulnerability and perform reconstruction attacks, an attack in which pseudonymised data is reverse-engineered to the original data by a variety of techniques.
Insecure Third-party plugins
When it comes to the functionality of LLMs, most, if not all of its functionalities are derived using third-party plugins. These third-party plugins from unknown senders are not guaranteed or checked. Since these plugins may have access to the internal workings, their low security can be exploited by malicious users.
Protecto assures data security compliance according to the GDPR which ensures good vetting and protection of any agents being used.
Compromised Chains of Supply
When it comes to the chain of supply of data analysis, it starts from data preprocessing, training the data and then testing the data before the LLM is even deployed. If any of these processes are compromised by malicious users, it may ruin the entire model. LLM Data Privacy models can be trained with different scenarios where there may be compromises in the supply chains, and deal with it appropriately.
Cybersecurity Threats
Since LLMs are resource-intensive, simple Denial of Service (DoS) or Distributed Denial of Service (DDoS) attacks will overwhelm them. Using automated scaling listeners and tracking digital footprints will help predict these attacks and prepare for them.
Protecto’s private SaaS-hosted server is extremely secure and impenetrable. Their agentless solution makes it easier to implement their services in your cloud data.

Autonomy Problems
Sometimes, after training the LLM Models, they’re left to their own devices with no updates. This autonomous nature will make it a monolith in time and be irrelevant and not have state-of-the-art security installed.
Protecto regularly update LLMs with a technique called RAG (Retrieval Augmented Generation) to ensure that your LLM data protection techniques are up to speed.
Over-dependence on solutions from LLMs
A very common problem with LLMs is their tendency to “hallucinate”. This makes them provide wrong predictions and answers. Malicious users can use this to their advantage by poisoning the training data, making these ‘hallucinations’ more frequent.
With granular access to the training data and RAG implementation, Protecto looks at the output generated by LLMs with a little bit of scepticism.
Leaking of Sensitive Information
Due to the many loopholes discussed above, there are many real-life cases in which sensitive information of the users has been divulged to other people. LLMs sometimes provide sensitive data when there are ‘bugs’ in the system or via prompt injections.
Protecto deals with that by feeding only tokenized data to their LLMs so that even in case of a security breach, they can only access the pseudonymized data and get little to no personal information about the users.
Theft of Models
Once the LLMs are deployed online, many malicious users and other people may try to replicate your LLM Data Security processes. This may end up with them finding vulnerabilities in your LLM and exploiting them.
Protecto’s granular access to the workings of LLMs and the data ensures this problem to the minimum because those with access to such sensitive data are vetted properly and have their experience speak for them.

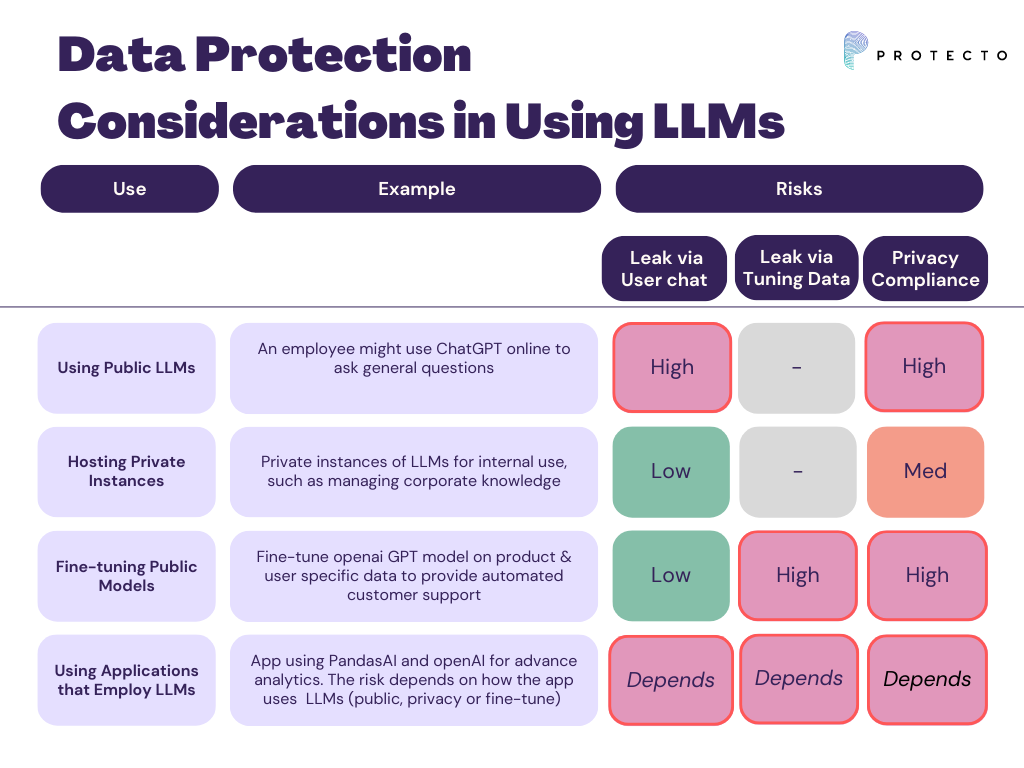
Using Public LLMs
- Application: Public models, such as ChatGPT, are used in various contexts due to their versatile capabilities.
- Example: An individual might use ChatGPT online to ask general questions or gather information on a topic.
- Data Protection Consideration: When interacting with public models, the data shared might be exposed to third parties. Employees might inadvertently share sensitive data, which can significantly impact the brand and business. Privacy compliance could be at risk if personal or proprietary information is shared. Users must exercise caution to mitigate this risk.
Hosting Private Instances
- Application: Businesses may host private instances of LLMs for internal use, such as managing corporate knowledge.
- Example: A company may use a privately hosted LLM to automate responses to frequently asked internal questions about compliance policies and procedures.
- Data Protection Consideration: Hosting LLMs privately reduces the risk of external data leaks.
Must Read: Top 13 LLM Vulnerabilities and its solution in Data Privacy
Fine-tuning Public Models
- Application: Fine-tuning a public model for a specific task, like customer support.
- Example: An organization may fine-tune ChatGPT on its product-specific data to provide automated customer support.
- Data Protection Consideration: While the risk of data leakage to the outside is relatively low, data might be exposed inadvertently during the model's interaction with internal users. Exposing customer information, salary, or sensitive business data can lead to serious issues. Therefore, businesses must establish strict data management practices and privacy compliance protocols during fine-tuning and deployment.
Using Applications that Employ LLMs
- Application: Tools or platforms that use LLMs for tasks
- Example: An app that uses an LLM to help users write essays or reports.
- Data Protection Consideration: The risk of data leakage varies depending on whether the application uses public, private, or fine-tuned LLMs. As a general rule, assuming a high level of risk is advisable. Applications must implement stringent data privacy measures and ensure robust security practices to uphold privacy norms.
Best Practices for Implementing LLM Security
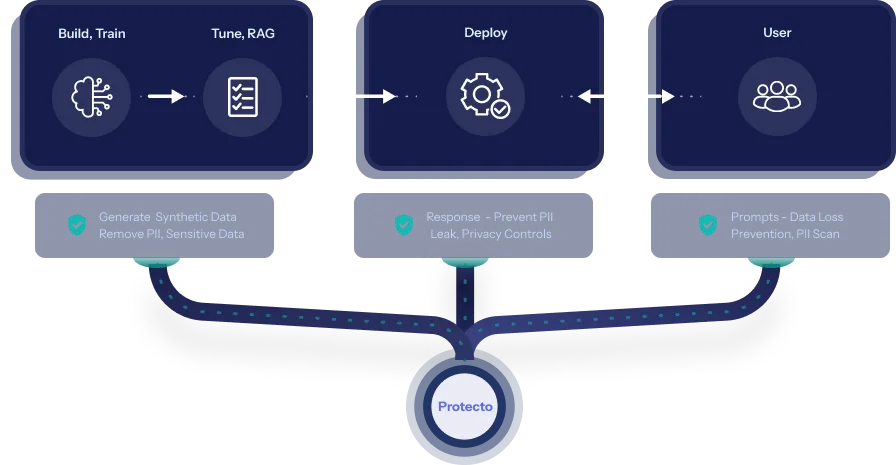
The best practice for implementing LLM Security is to provide proper countermeasures for the LLM Data Security applications. Constantly training and adding new data points and retraining the data is very resource-intensive. There have been other ways using fewer resources to implement LLM in Data Privacy. These are using the concepts of intelligent Prompting and RAG (Retrieval Augmented Generation).

Secure Your Digital Landscape: Getting Started Now with the Top LLM Data Privacy Solution
Protecto provides a detailed solution in the field of LLM Data Protection. They use Advanced AI to go through your chat logs and mask any sensitive data or PII (Personally Identifiable Information) to protect your information from Generative AI chatbots such as ChatGPT or Gemini.
With their cloud data protection, you can experience Data Privacy in the cloud, even in multiple cloud platforms since their solutions are supported for multiple platforms.

Get a free demo from Protecto to use their services for your benefit. It is free and they only require your business email.
In conclusion, navigating the data protection and privacy compliance concerns that come with the versatility of LLMs is crucial. Whether an organization is using public models, hosting private instances, fine-tuning models, or employing LLM-powered applications, robust data management strategies and strict compliance protocols are essential.
That said, managing these complexities can be challenging. Hence, to help organizations leverage LLMs more securely and responsibly, we have designed the "Protecto AI Trust Layer". This advanced AI system integrates seamlessly into your existing workflows, providing an additional layer of data security and privacy protection when interacting with LLMs.
With Protecto, you can confidently mitigate the risk of data leaks and breaches, ensuring your LLM usage remains compliant with the strictest privacy laws. As data protection becomes an ever more important differentiator, Protecto's AI Trust Layer provides the proactive solution that organizations need to unlock the full potential of LLMs, while safeguarding user privacy and fostering trust.
Prevent millions of $ of privacy risks. Learn how.
We take privacy seriously. While we promise not to sell your personal data, we may send product and company updates periodically. You can opt-out or make changes to our communication updates at any time.





