As organizations increasingly rely on cloud data platforms, securing PII (Personally Identifiable Information) has become more critical than ever. Snowflake, a robust cloud-based data warehouse, stores and processes vast amounts of sensitive information. With the rise in data breaches and stringent regulations like GDPR and CCPA, safeguarding PII data in Snowflake is essential to ensure data privacy and compliance.
Here, we explore the best practices for securing Snowflake PII, helping organizations protect their most sensitive data while meeting regulatory demands. We’ll cover key security features and advanced techniques for adequate data protection within the Snowflake platform.
Understanding PII and Its Importance
Personally Identifiable Information (PII) refers to any data that can identify an individual, such as names, social security numbers, and contact details. In today’s digital world, protecting PII is vital for individuals and organizations. Mismanagement of this data can lead to identity theft, financial fraud, and legal penalties.
In Snowflake, where vast amounts of sensitive data are stored, securing PII data is crucial for compliance with regulations like GDPR, CCPA, and other global privacy laws. These regulations mandate strict measures for handling and protecting PII, making it essential for organizations to prioritize Snowflake data protection.
Failure to protect PII leads to compliance issues and erodes customer trust. Therefore, safeguarding PII in Snowflake ensures legal adherence and the security of individual privacy.
Snowflake’s Security Capabilities for PII
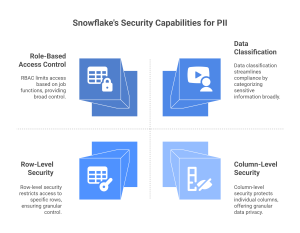
Snowflake offers a robust security framework to protect PII through its advanced access control and data privacy features. Two critical elements of this framework are role-based access control (RBAC) and discretionary access control (DAC). With RBAC, administrators can assign users specific roles, limiting their access to PII data based on the job functions. DAC further enhances this by allowing data owners to manage who can view or modify specific datasets. Together, these tools ensure that only authorized personnel can access sensitive data.
Snowflake row-level and column-level security provides even more granular control. Row-level security restricts access to specific rows within a dataset based on a user’s role or attributes, ensuring that employees only access data relevant to their tasks. Column-level security protects individual columns containing sensitive information, allowing organizations to hide or mask specific columns while granting access to others. This is essential for securing sensitive information like social security numbers or email addresses.
Snowflake’s data privacy policies also include built-in features for data classification. Snowflake allows organizations to quickly identify and apply protections to sensitive information like PII by categorizing data into different types. This policy-based approach helps streamline compliance with regulations such as GDPR and CCPA, ensuring that Snowflake data protection measures align with industry standards.
These capabilities and a comprehensive encryption mechanism make Snowflake an ideal platform for protecting personally identifiable information in large-scale cloud environments.
Interested Read: Best Practices for Protecting PII Data
Best Practices for Securing Snowflake PII
Securing personally identifiable information (PII) in Snowflake requires a combination of technical and organizational measures. Adopting best practices ensures the safety of sensitive data and helps meet compliance requirements. These practices focus on access control, encryption, monitoring, and ongoing audits.
Implement Role-Based and Attribute-Based Access Control
Role-based access control (RBAC) is fundamental for protecting PII in Snowflake. Assign specific roles to users based on their responsibilities within the organization. For example, limit database access to only those team members who need it for their work. This minimizes the risk of unauthorized access and reduces the overall attack surface.
For more granular control, use attribute-based access control (ABAC), which considers additional factors such as user attributes and environmental conditions. This flexibility allows you to set rules based on data classification, user location, and device security status, ensuring stricter control over access to sensitive PII.
Interested Read: Role-based access control for LLM sensitive data
Use Strong Data Encryption
Snowflake’s built-in encryption features play a critical role in protecting PII. All data is encrypted at rest and in transit, but to further enhance security, use end-to-end encryption. End-to-end encryption ensures that sensitive information remains encrypted from when it is collected until it reaches the end user, eliminating potential vulnerabilities during data transmission.
Implement key management policies to control encryption keys. Snowflake supports customer-managed keys (CMK), allowing you to manage and rotate keys based on your organization’s security policies. This adds another layer of security and control over sensitive data.
Read more: Pseudonymization vs Anonymization: Key Differences, Benefits, & Examples
Mask Sensitive Data
Data masking is a critical tool in protecting PII in non-production environments. Developers often need access to data for testing and troubleshooting, but sharing real sensitive data can expose PII. Data masking allows you to hide or replace PII with fictional but realistic data. This ensures that sensitive information is protected, even in development or testing environments.
Snowflake provides dynamic data masking, allowing organizations to apply different masking policies depending on the user or role accessing the data. This ensures that masked data is revealed only to authorized users.
Interested Read: Protect Sensitive Data with Key Privacy Enhancing Techniques
Regular Auditing and Monitoring
Continuous monitoring and auditing are vital for ensuring that security controls remain effective. Snowflake offers comprehensive logging and monitoring capabilities that track every action taken on the platform, including logins, data access attempts, and queries involving PII.
Set up automated alerts for suspicious activities, such as multiple failed login attempts or unusually high-volume data extractions. Proactively monitoring access and usage patterns helps detect potential breaches early. Conduct regular audits to ensure compliance with data protection laws like GDPR and CCPA, which often require proof that PII is secured and access is restricted.
Snowflake’s Event Tables and Account Usage views are valuable tools for tracking access patterns and identifying potential security gaps. Integrate these tools into your organization’s security information and event management (SIEM) systems for real-time tracking.
Implement Data Retention and Deletion Policies
Snowflake allows you to configure data retention policies based on your organization’s compliance requirements. For PII, establish clear guidelines on how long the data should be retained. Retaining sensitive data longer than necessary increases the risk of unauthorized access or exposure.
Develop and enforce data deletion policies to ensure that outdated or unused PII is removed from your systems. This reduces the risk of a breach and helps meet regulatory requirements for data minimization.
Time Travel is a feature in Snowflake that allows organizations to restore data to previous versions. While this is useful for operational recovery, it’s essential to ensure that sensitive PII is deleted or overwritten in old snapshots, especially when complying with regulations requiring data erasure on request.
Ensure Compliance with Data Protection Regulations
Compliance with regulations like GDPR, CCPA, and HIPAA is critical when managing PII in Snowflake. These laws mandate strict measures for data protection and enforce individuals’ rights to control their personal data.
Snowflake’s data classification tools can help you identify and protect PII. Use these tools to label and tag sensitive data, making it easier to apply appropriate security measures. Review and update your PII protection strategies to align with changing regulatory requirements.
Advanced Techniques for Protecting PII in Snowflake
De-Identification and Anonymization Techniques
Advanced techniques such as data masking, tokenization, and hashing can be used to protect PII in Snowflake. Data masking hides sensitive information by substituting it with fictitious data, ensuring unauthorized users can’t access the original values. Tokenization replaces sensitive PII with randomly generated tokens, which can only be mapped back to the original data via a secure token vault. Hashing converts PII into a fixed-length value, making it nearly impossible to retrieve the original data without the correct key. These techniques enhance Snowflake data protection by limiting the exposure of sensitive information.
Using Third-Party Data Security Tools
In addition to Snowflake’s built-in security features, integrating third-party tools can further protect PII in Snowflake. These tools provide additional layers of encryption, access controls, and monitoring to ensure that sensitive data is not exposed. Popular frameworks offer real-time threat detection and compliance monitoring, which is crucial for maintaining data security and privacy standards.
Regulatory Compliance and Data Privacy Standards
Importance of Compliance
Compliance with data privacy laws like GDPR, CCPA, and HIPAA is crucial when handling personally identifiable information (PII). These regulations impose strict requirements for securing sensitive data and govern how organizations collect, store, and process PII. Non-compliance can lead to heavy fines and reputational damage. Adhering to these standards ensures that PII is handled responsibly, protecting organizations and their customers from data breaches.
Interested Read: PII Compliance Checklist: Safeguard Your PII Data
Aligning Security Measures with Data Privacy Standards
Organizations must align their PII security practices with data privacy standards to ensure compliance. This includes implementing encryption, access controls, and regular audits to secure PII data. Security frameworks should be flexible enough to meet the evolving requirements of different regulations while ensuring that PII remains protected across all environments, including cloud platforms like Snowflake.
Conclusion
Securing personally identifiable information (PII) in Snowflake is essential for maintaining data privacy and compliance with regulations. Implementing best practices, such as encryption, access controls, and de-identification techniques, enhances data protection. Additionally, aligning security measures with regulatory standards like GDPR and CCPA is crucial. Organizations must continuously evaluate their security configurations to ensure they effectively protect PII. By adopting these strategies, businesses can mitigate risks and strengthen their overall data security posture.
Take proactive steps to safeguard your PII in Snowflake today.



